A hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. Hacker can use any os for hacking. Window, Linux, MacOS. If you want to learn hacking or do hacking you need to use command line for work faster. In this article, PastFutur share some of the best CMD command that are widely used in Hacking purposes in Windows 10. Every hacker must know this cmd command for hacking.
What is CMD or Command Prompt or CMD command?
CMD is the default command-line interpreter for the OS/2, eComStation, ArcaOS, Microsoft Windows (Windows NT family and Windows CE family), and ReactOS operating systems. The name refers to its executable filename. It is also commonly referred to as cmd or the Command Prompt, referring to the default window title on Windows. The implementations differ on the various systems but the behavior and basic set of commands is generally consistent.
cmd.exe is the counterpart of COMMAND.COM in DOS and Windows 9x systems, and analogous to the Unix shells used on Unix-like systems. The initial version of cmd.exe for Windows NT was developed by Therese Stowell. Windows CE 2.11 was the first embedded Windows release to support a console and a Windows CE version of cmd.exe. On Windows CE .NET 4.2, Windows CE 5.0 and Windows Embedded CE 6.0 it is also referred to as Command Processor Shell. The ReactOS implementation of cmd.exe is derived from FreeCOM, the FreeDOS command line interpreter. (Accounting to wikipedia.)
Why CMD is important?
CMD Command Prompt is a command line interpreter application available in most Windows operating systems. It’s used to execute entered commands. Most of those commands automate tasks via scripts and batch files, perform advanced administrative functions, and troubleshoot or solve certain kinds of Windows issues.
Sometimes accidentally we delete some necessary files from our PC. Sometimes we cannot recover them in time. Unfortunately, there are a lot of data recovery software but the others all are paid systems. But Recuva is a free data recovery software. You can recover your lost data very easily by using it.
Why Hacker use CMD?
Not only hacker, but many IT professionals use the cmd Command commandline because it gives them a environment of tools that can be combined. When working with the commandline you can write scripts that run your tools automatically, you can also easily take the output of one command and use it as the input for another command. CLI tools also use arguments for their configuration, you can store those in a file and re-use them.It is also a bit cheaper to develop CLI-tools, you simply don’t have to build the GUI and maintain cross-platform compatibility for your GUI, although that is not the main reason.
Ransomware decrypt, Ransomware is one of the most dangerous malicious or virus type software. It can infect your computer’s files and suddenly it displays messages demanding a fee.
How to get CMD or Command Prompt?
CMD or Command Prompt build in installed in Window operating system. You can open the Command Prompt by pressing ⊞ Win + R to open the Run box and typing cmd . Windows 8 or 10 users can also press ⊞ Win + X and select Command Prompt from the menu.

Run box comming and type cmd and hit enter.
CMD Command Prompt

Most useful CMD Command for Hacker.
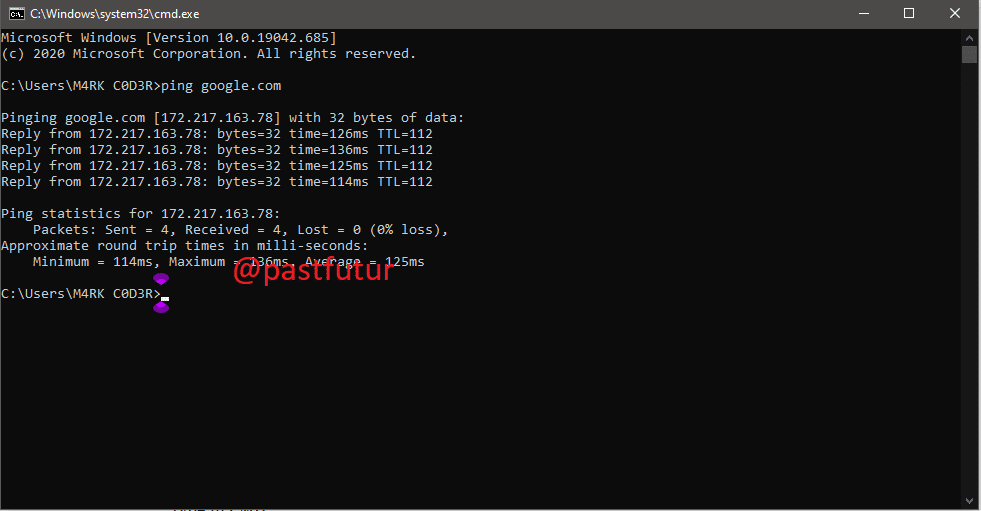
1. PING cmd Command:
This command uses your internet connection in order to send some packets of data to a specific web address then these packets are sent back to your PC. It helps you to know if the host you pinging is alive. You can use the Ping command whenever you need to verify that the host computer can connect to the TCP/IP network and its resources.
For example: you can type in Command prompt ping 8.8.8.8 which belongs to Google. You can replace “8.8.8.8” to “www.google.com” or something else which you want to ping.
2. nslookup cmd Command:
It is a network administration command-line tool that helps you to obtain domain name or IP address mapping for any specific DNS record. Suppose you have a website URL but want to know its IP Address, you can simply type in CMD.
For example: nslookup www.google.com (Replace Google.com with your website URL of which you want to find the IP address)
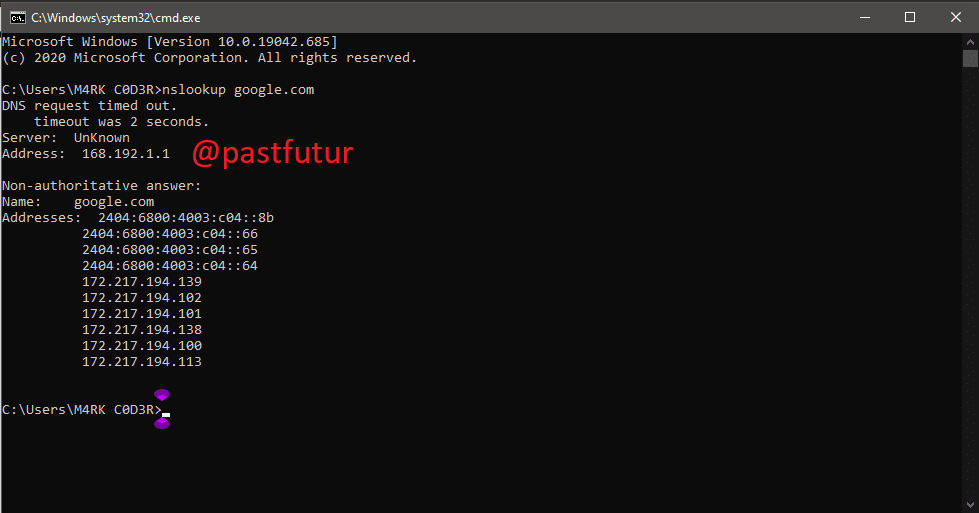
3. Tracert cmd command:
You can say Trace Route like its name it allows users to trace the route than an IP packed has taken to reach a destination. The command calculates and displays the amount of time each hop took to reach a destination. You just need to type in CMD.
For example: tracert x.x.x.x (if you know the IP Address) or else you can type tracert www.google.com (If you don’t know the IP address)
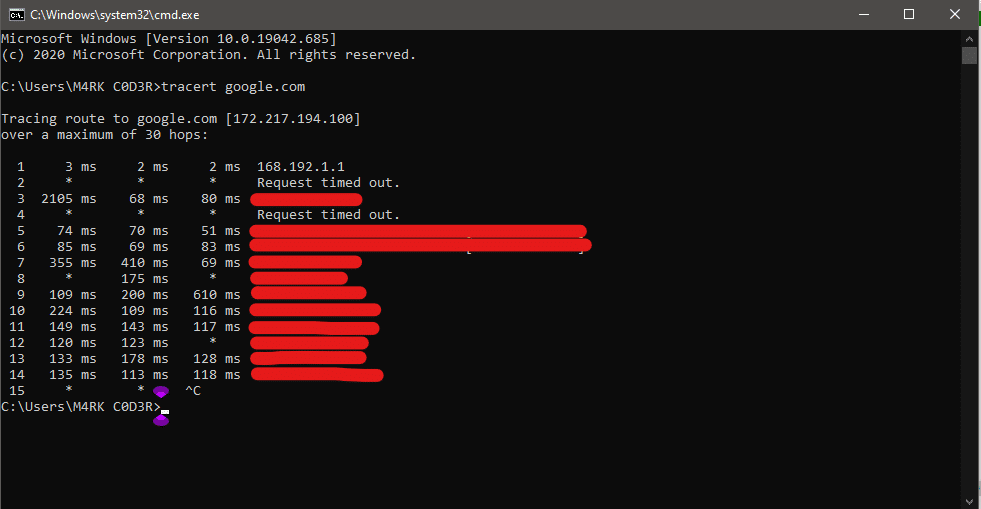
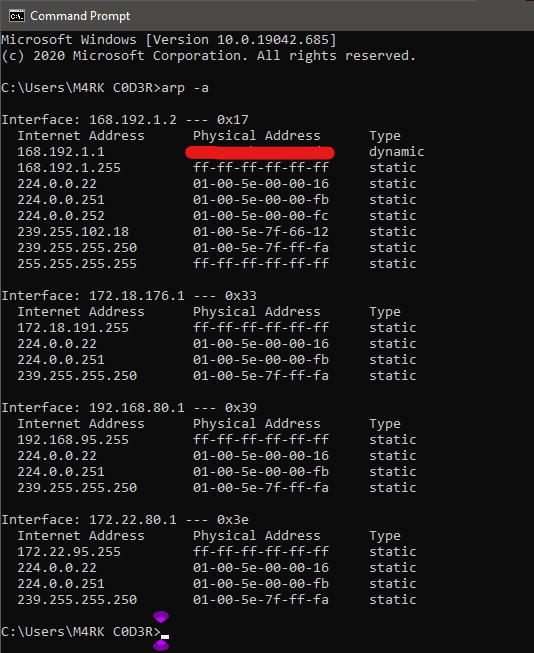
4. Arp cmd command:
This command helps you to modify the ARP cache. You can run an arp-a command on each computer to see whether the computers have the correct MAC address listed for each other to ping each other succeed on the same subnet. This command also helps users to find out if anyone has done arp poisoning in their LAN.
For example: You can try typing arp -a in command prompt.
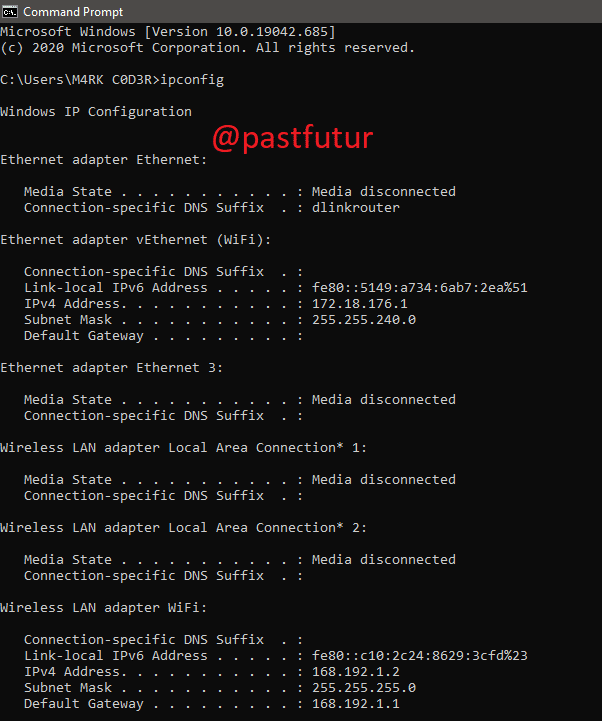
5. ipconfig cmd command:
This is the command which shows every useful thing. It will show you IPv6 address, temporary IPv6 address, IPv4 address, Subnet Mask, Default gateway and all other things that you want to know.
For example: You can type in command prompt ipconfig or ipconfig/all
The registry is those files where some of the files that remain after uninstalling software on your personal or any computer. It is a database system that contains all the information, general settings, etc. There are many software entries inside your registry.
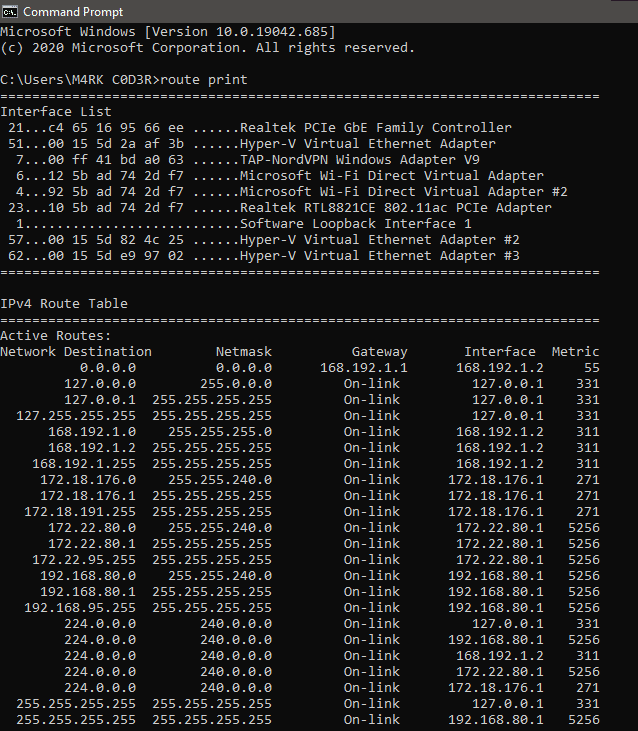
6. Route print cmd command:
It is a command which is used to view and manipulate the IP routing table in the Microsoft Windows operating system. This command will show you routing table, metric and interface.
For example: You can type in command prompt route print
7. Net view cmd command:
This command displays the whole list of resources, computers or domains that are shared by the specified computer.
For example: You can type in command prompt net view x.x.x.x or computername
8. Net User cmd command:
Well, this command is used to modify changes to user accounts on a computer. You can add, remove users with the help of this command
For example: You can use these commands while using net user net user [<UserName> {<Password> | *} [<Options>]] [/domain]
net user [<UserName> {<Password> | *} /add [<Options>] [/domain]]
net user [<UserName> [/delete] [/domain]]
Final Though.
Command Prompt is a command line interpreter application available in most Windows operating systems. It’s used to execute entered commands. Most of those commands automate tasks via scripts and batch files, perform advanced administrative functions, and troubleshoot or solve certain kinds of Windows issues. If you want be a hacker then you must practice to use cmd command or terminal.
Facebook: https://www.facebook.com/pastfutur.official
Twitter: https://twitter.com/PastFutur
Get us
A security hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. The purpose of cyber security services is help prevent cyber attacks, breaches of data and identity theft that can risk the management of an organization. Ransomware, malware, social engineering and phishing are the types of cyber threats that may endanger the information and other assets in your computer. Besides protecting us from cyber threats, it has many other benefits like increase in productivity, gaining customer confidence, protection of customers and the reduction of chances of the website going. Many companies have the best cyber security services to aid this purpose not only this we can protect ourselves in many ways too.
Thank You: https://m.facebook.com/m4rkc0d3r/