Car Hacking – Using & Run Tool for Linux – Guide for Penetration Tester – ICS Simulator Part-2
Car Hacking – Install & Setup Tool for Linux – ICS Simulator Part-1
Welcome back, my aspiring automobile cyber warriors! Automobile hacking is the cutting edge of the hacking discipline! Automobile and other vehicle hacking could have dramatic effects on society as we know it. Imagine a cyber war scenario where the opposing generals employ hackers to commandeer the adversaries tanks, jeeps and other vehicles. Or a bit more mundane, imagine a world where hackers can open, start and control your vehicle!
1. Basic tools to display, record, generate and replay CAN traffic
- candump : display, filter and log CAN data to files
- canplayer : replay CAN logfiles
- cansend : send a single frame
- cangen : generate (random) CAN traffic
- cansniffer : display CAN data content differences (just 11bit CAN IDs)
2. CAN access via IP sockets
- canlogserver : log CAN frames from a remote/local host
- bcmserver : interactive BCM configuration (remote/local)
- socketcand : use RAW/BCM/ISO-TP sockets via TCP/IP sockets
3. CAN in-kernel gateway configuration
- cangw : CAN gateway userpace tool for netlink configuration
4. CAN bus measurement and testing
- canbusload : calculate and display the CAN busload
- can-calc-bit-timing : userspace version of in-kernel bitrate calculation
- canfdtest : Full-duplex test program (DUT and host part)
Step 1: Start the cansniffer
Let’s begin by sniffing the CAN traffic using cansniffer. With this utility you must specify the interface (vcan0, in our case) and if you want to see the colorized output, use the -c option.
cansniffer -c vcan0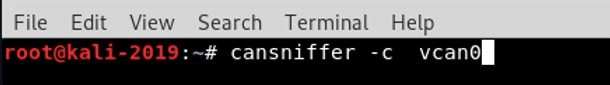
As soon as you enter this command, you should begin to see the CAN network traffic displayed in your terminal similar to the screenshot below.
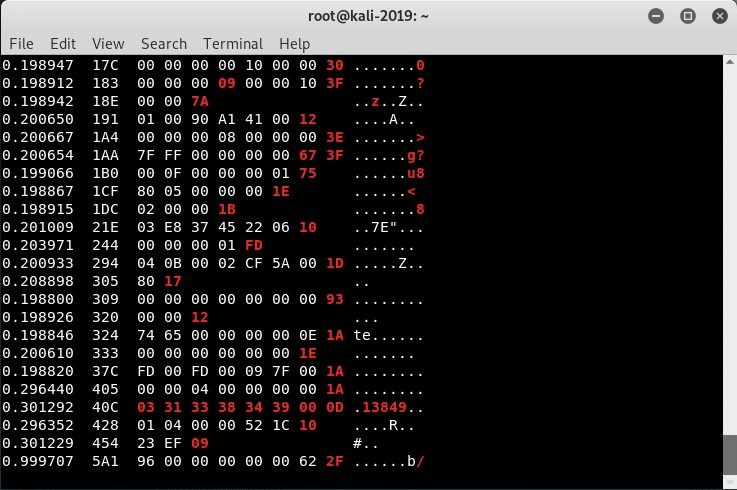
When we use the -c option, the values that are changing turn a red color to help us identify these key values.
Step 2: Use cansniffer to Filter for Specific Traffic
Rather than watch all the traffic go past our terminal, we can filter traffic similarly to the more widely used sniffer, Wireshark.
Let’s look at the help screen in cansniffer to learn to do so.
cansniffer -h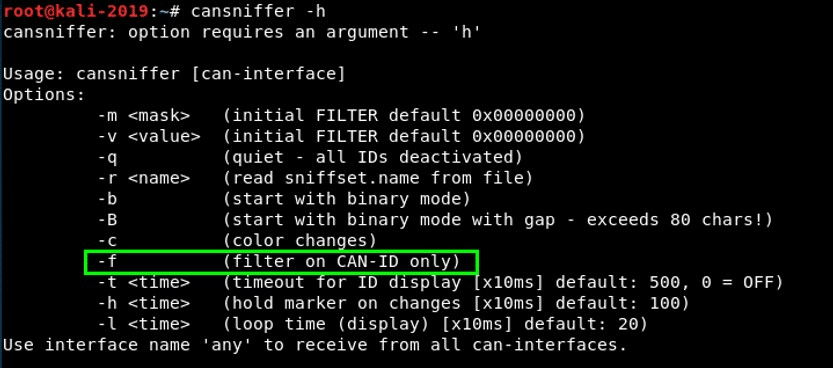
Then, if we only wanted to see traffic from ID=161, we could enter;
cansniffer -c vcan0Once the sniffer has started, we can then enter;
-000000+161It’s important to note that when you enter the above commands, they will not appear on the screen. Once you have entered the ID number, the sniffer will begin to filter out all traffic but those with the ID= 161

As you can see in the screenshot above, cansniffer now displays just the data for ID=161
Step 3: Using candump to capture CAN traffic
While the cansniffer is capable of sniffing traffic on the CAN network similarly to Wireshark, the candump utility in can-utils is capable of capturing CAN traffic and storing it into a file for analysis or replay at a later time.
To do so, we can need only to use the -l option to log and the -c option to colorize the output.
candump -c -l vcan0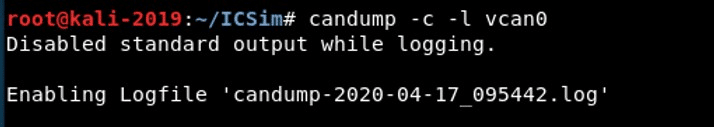
If we want to log AND view the output, we can use the -s 0 option (silent mode 0). In addition, if we want to output to be converted from hex to ASCII (human readable), we can add the -a (ASCII) option. This starts candump in colorize mode, with ASCII output, storing the data into a log file and simultaneously sending it to the terminal (stdout).
candump -c -l -s 0 -a vcan0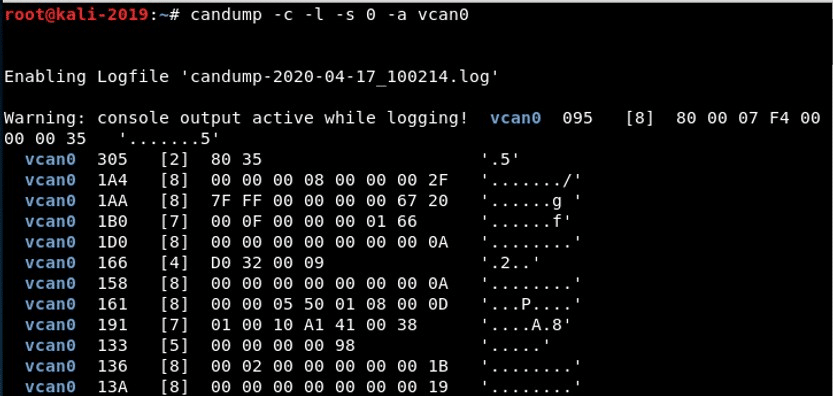
Step 4: Using canplayer
We also have another key CAN network tool, canplayer. This tool enables us to “play” the output from candump. So, we could capture the data from the CAN network and then replay it on the network. We only need to use the -I option followed by the name of the log file from candump.
canplayer -I candump-xxxxxxxxxxx.log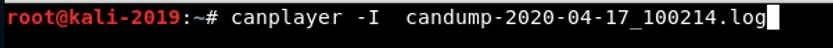
Step 5: Using cansend to Send Custom Frames
Finally, we have the cansend tool. This tool enables us replay a specific frame or to send a custom crafted CAN frame. If we want to resend a single frame we isolated above with ID=161,

we do so by entering;
cansend vcan0 161#000005500108000dWhere:
- vcan0 is the interface
- 161# is the frame ID
- 000005500108000D is the data we want to send

Now, when we hit enter, the custom CAN frame will be sent over the network. I hope it is obvious that when we reverse engineer the network, this is the command we will use to initiate the actions we desire on the CAN network such as; accelerate, open the door, initiate brakes, etc.
Summary
Now that we have installed the ICS Simulator and understand the basics of the key can-utils tools, we can now begin to use these tools to reverse engineer the CAN bus on our ICS Simulator and take control of the vehicle! Car hacking
Facebook: https://www.facebook.com/pastfutur.official
Twitter: https://twitter.com/PastFutur
Linkedin: https://www.linkedin.com/company/pastfutur
Telegram: https://t.me/pastfutur_official