Car Hacking – Install & Setup Tool for Linux – Guide for Penetration Tester – ICS Simulator Part 1
Welcome back, my aspiring automobile cyber warriors! Automobile hacking is the cutting edge of the hacking discipline! Automobile and other vehicle hacking could have dramatic effects on society as we know it. Imagine a cyber war scenario where the opposing generals employ hackers to commandeer the adversaries tanks, jeeps and other vehicles. Or a bit more mundane, imagine a world where hackers can open, start and control your vehicle!
In this tutorial we will set up a simulation environment where you can use some of this knowledge to analyze and hack a simulated vehicle.
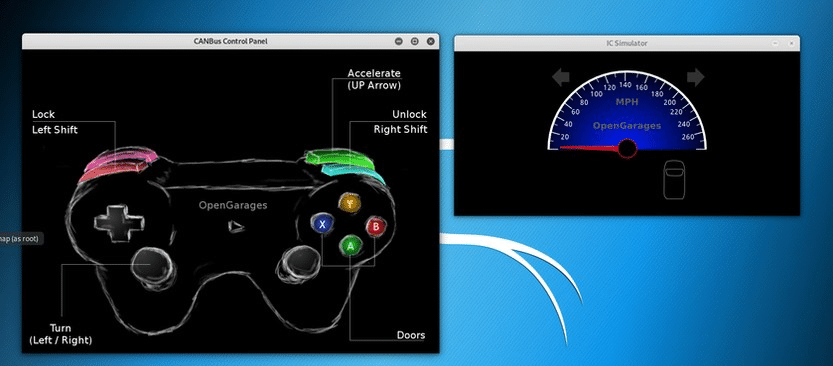
This CAN Bus simulator was developed by Craig Smith at Open Garages and the author of The Car Hackers Handbook by No Starch Press.
Step 1: Install Dependencies for Card Hacking
The first step is to install the necessary dependencies into your Kali system.
apt-get install libsdl2-dev libsdl2-image-dev -y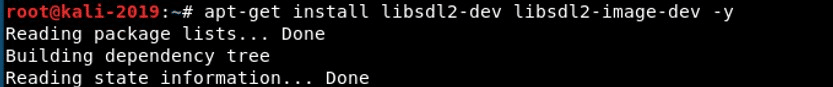
Step 2: Install Can Utils
The next step is to install the CAN utils. These are a set of Linux-native utilities developed by Bosch of Germany. If you followed my second tutorial in the series, you have likely already installed these utilities. If not, you can do so now by downloading and installing them from the Kali repository.
apt-get install can-utils -y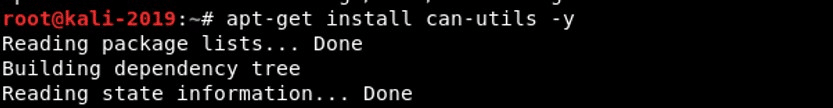
Step 3: On a virtual CAN interface
You can run the following commands to setup a virtual can interface
Chack your Network Type ifconfig
sudo modprobe cansudo modprobe vcansudo ip link add dev vcan0 type vcansudo ip link set up vcan0Step 4: Download ICSim for Card Hacking
Craig Smith, author of The Car Hackers Handbook and founder of opengarages.org has developed a small CAN simulator we will download and install next. You can clone it from github.com here.
git clone https://github.com/zombieCraig/ICSim
Next, we navigate to the newly created directory, ICSim.
cd ICSim
When we do a long listing on that directory, we can see numerous files. At this point, we need to execute the setup_vcan.sh script. This is a simple BASH script that loads the new kernel modules, can and vcan, using modprobe (for more on kernel modules, see Chapter 8 of Linux Basics for Hackers) and then creates a virtual CAN interface, vcan0.
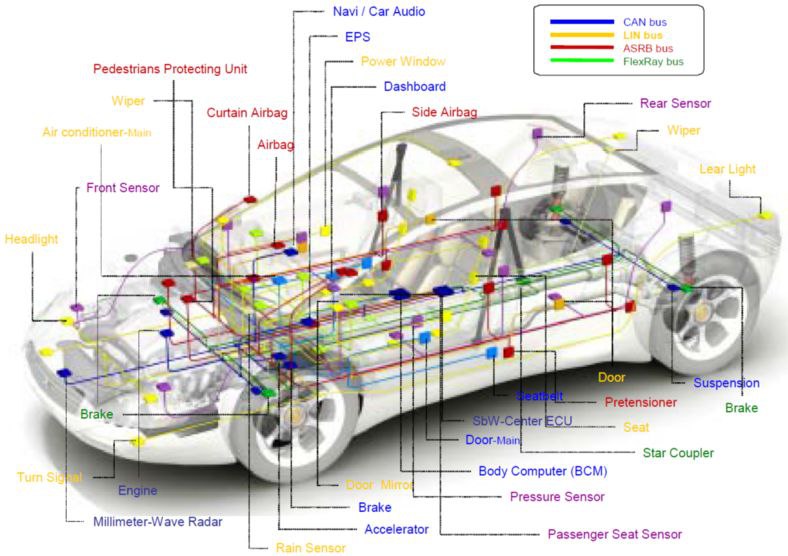
Hacking Tools are computer programs and scripts that help you find and exploit weaknesses in computer systems, web applications, servers and networks. There are a variety of such hack tools available in the market. Some of them are open source while others are commercial solution.Following is a handpicked list of Top 20 Best Ethical Hacking Tools, with their popular features and website links. The list contains both open source(free) and commercial(paid) software.
Step 5: Download Hides Files
make./setup_vcan.sh
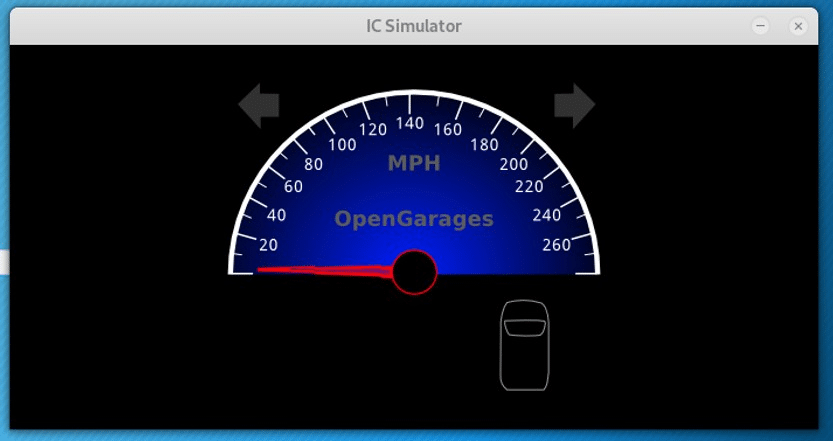
To start the instrument panel of our simulated vehicle, we simply need to execute icsim followed by the name of the virtual CAN interface, in this case, vcan0.
./icsim vcan0The instrument panel should appear on your desktop like below. It includes a speedometer, turn signal and a virtual vehicle silhouette similar to modern vehicles that indicate open and closed doors for the driver.
To start the controller of this vehicle, enter;
./controls vcan0This should open the controller on your desktop as seen below.
SQL Injection Hacking. The use of databases for various data storage management greatly increases in web app development as time goes on. The database facilitates interaction between users and servers. The database (or in terms of Database Management System abbreviated to DMBS) provides various benefits including data input and storage, retrieval of large information, and the ease of compiling and grouping information.
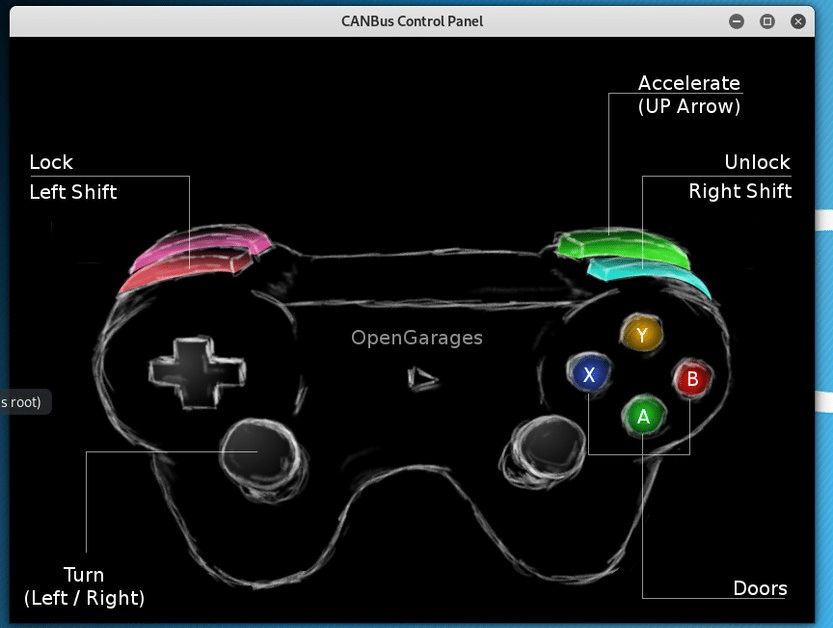
If you have a game controller connected to your Kali system, you can now use it to “drive” your simulated car. If not, you can use the following keyboard combinations.
Car Hacking – Using & Run Tool for Linux – Guide for Penetration Tester – ICS Simulator Part 2
Facebook: https://www.facebook.com/pastfutur.official
Twitter: https://twitter.com/PastFutur
Linkedin: https://www.linkedin.com/company/pastfutur
Telegram: https://t.me/pastfutur_official
Copyright: OnlineHacking.xyz