This article is the part of Android Hacking tutorial; it covers step by step guide to exploiting Android ADB to get the persistent connection back to the attacker machine. You can use the Kali Linux as an attacker machine, exploit the ADB, and set up the Backdoor channel after hacking android devices.
Android Hacking ADB using the Ghost Framework
The ghost framework is not a hacking tool, and we are not hacking the android device. Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to access an Android device remotely. So, this is a post-exploitation tool that gives a persistent connection and works as a backdoor.
Passwords are always our first and, in cases, sole line of protection from attackers. If an intruder does not possess direct accessibility to a system, they may also use the remote desktop interface to connect to a server or a system. Windows Password hacking and cracking are the most important topic amongst hackers and pentesters. This article discusses the steps to capture NTLM hash of a windows machine and how to crack this password using John the Ripper.
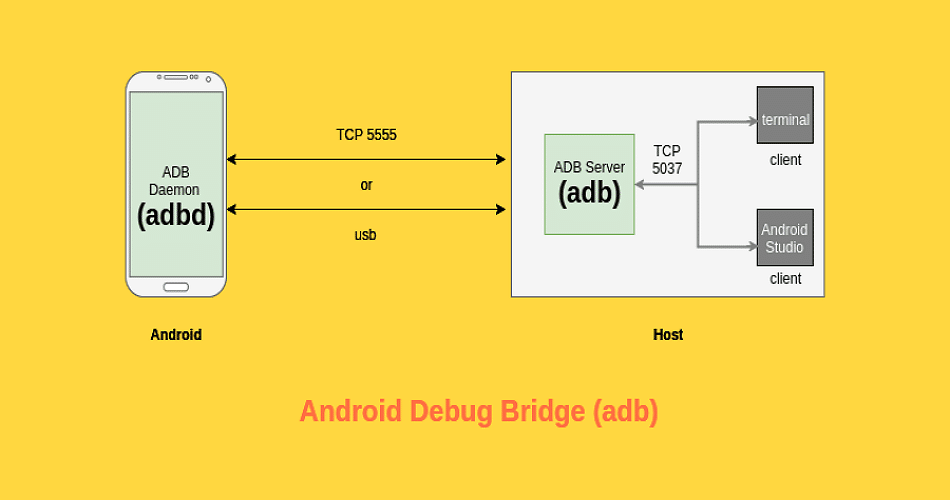
So, what is ADB? ADB or Android Debug Bridge is a feature or command-line tool released by Android to connect and operate Android-based devices remotely. But, the hackers exploit this feature and connect the hacked android devices remotely.

ADB allows you to do things on an Android device that may not be suitable for everyday use, For example, you can install apps outside of the Play Store (waoooo; it means you can install whatever you want to), it also gives access to the hidden features, and bring up a Unix shell so you can issue commands directly on the device. I mean, you own it.
Install Ghost Framework in Kali Linux for Android Hacking
Let’s start by installing the ghost in the Kali Linux. You can download or simply clone it using the git command.
git clone https://www.github.com/entynetproject/ghost.git
CMD Command for Hacker [Most uses]
A hacker is someone who explores methods for breaching defenses and exploiting weaknesses in a computer system or network. Hackers can use any os for hacking. Window, Linux, MacOS. If you want to learn hacking or do hacking you need to use command line for work faster. In this article, PastFutur share some of the best CMD command that are widely used in Hacking purposes in Windows 10. Every hacker must know this cmd command for hacking.
After downloading, we need to get into the directory.
cd ghostlsThere you can see all the files and directories. We need this install script to install the program.
./install.sh
Now, the installation is complete, let’s run the program.
./ghost
This ghost framework shares the similar commands to the Metasploit. So, we can execute those commands; for example, help to see all the options.
HelpSo, there you can see all the commands with a brief description.
How to Install Kali NetHunter in any Android Phone
The Kali Linux NetHunter project is the first Open Source Android penetration testing platform for Nexus devices, created as a joint effort between the Kali community member “BinkyBear” and Offensive Security. NetHunter supports Wireless 802.11 frame injection, one-click MANA Evil Access Point setups, HID keyboard (Teensy like attacks), as well as BadUSB MITM attacks – and is built upon the sturdy shoulders of the Kali Linux distribution and toolsets. Whether you have a Nexus 5, Nexus 6, Nexus 7, Nexus 9, Nexus 10 or OnePlus One we’ve got you covered. Our freely downloadable images come with easy to follow installation and setup instructions to get you up and running in no time at all.
Now let’s use the connect command to connect the remote android device as I said that it exploits ADB. So, make sure that the ADB port 5555 is open.

If you have hacked this device; then simply open the port.
So, demonstration I will look into the shodan for ADB enabled device.
And, then pick an IP to connect.
connect IP

Now we are connected; it means we got another session, and we can reconnect to the hacked device again, as long as the port is open.
Now, we can do many things. For example, we can record the screen of the phone; we can install or uninstall an app. We can also do port forwarding to create any other reverse connection. So, many things. Even we can remove the device password.
So, let’s check the app list. Sys info and many things can be done. But, the most important thing is to install your backdoor (since you have the ability now); install your backdoor for future and persistent connection.

So this is how the ghost framework exploits the Android ADB and gives another persistent connection to any android phone remotely.
Facebook: https://www.facebook.com/pastfutur.official
Twitter: https://twitter.com/PastFutur
Linkedin: https://www.linkedin.com/company/pastfutur

강남안마시술소중계업체